How To Return Account And Its Associated Contacts In Apex Rest Services
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical back up.
Tutorial: Configure HTTPS on a Front Door custom domain
This tutorial shows how to enable the HTTPS protocol for a custom domain that'south associated with your Forepart Door under the frontend hosts department. By using the HTTPS protocol on your custom domain (for example, https://world wide web.contoso.com), yous ensure that your sensitive data is delivered securely via TLS/SSL encryption when it'southward sent beyond the internet. When your web browser is connected to a spider web site via HTTPS, it validates the web site'southward security certificate and verifies it's issued by a legitimate certificate say-so. This process provides security and protects your web applications from attacks.
Azure Front end Door supports HTTPS on a Front Door default hostname, past default. For example, if you create a Front Door (such every bit https://contoso.azurefd.net), HTTPS is automatically enabled for requests made to https://contoso.azurefd.net. Withal, once you onboard the custom domain 'www.contoso.com' you'll need to additionally enable HTTPS for this frontend host.
Some of the primal attributes of the custom HTTPS feature are:
-
No extra cost: There are no costs for document acquisition or renewal and no actress cost for HTTPS traffic.
-
Elementary enablement: I-click provisioning is available from the Azure portal. You tin can also utilize REST API or other developer tools to enable the feature.
-
Consummate certificate management is available: All certificate procurement and direction is handled for you. Certificates are automatically provisioned and renewed before expiration, which removes the risks of service interruption considering of a certificate expiring.
In this tutorial, you learn how to:
- Enable the HTTPS protocol on your custom domain.
- Use an AFD-managed document
- Utilize your own certificate, that is, a custom TLS/SSL document
- Validate the domain
- Disable the HTTPS protocol on your custom domain
Prerequisites
Before you can consummate the steps in this tutorial, y'all must first create a Front end Door and with at to the lowest degree i custom domain onboarded. For more information, see Tutorial: Add together a custom domain to your Front Door.
TLS/SSL certificates
To enable the HTTPS protocol for securely delivering content on a Front Door custom domain, you must use a TLS/SSL certificate. You tin cull to apply a certificate that is managed by Azure Front Door or utilize your ain document.
Option 1 (default): Use a certificate managed past Front Door
When you use a certificate managed by Azure Forepart Door, the HTTPS characteristic can be turned on with just a few clicks. Azure Forepart Door completely handles certificate management tasks such every bit procurement and renewal. Later on you enable the feature, the process starts immediately. If the custom domain is already mapped to the Front Door's default frontend host ({hostname}.azurefd.net), no further activeness is required. Front Door volition process the steps and complete your asking automatically. However, if your custom domain is mapped elsewhere, y'all must use email to validate your domain buying.
To enable HTTPS on a custom domain, follow these steps:
-
In the Azure portal, scan to your Front Door profile.
-
In the list of frontend hosts, select the custom domain you lot want to enable HTTPS for containing your custom domain.
-
Nether the section Custom domain HTTPS, select Enabled, and select Forepart Door managed every bit the document source.
-
Select Save.
-
Continue to Validate the domain.
Note
- For AFD managed certificates, DigiCert'due south 64 character limit is enforced. Validation will fail if that limit is exceeded.
- Enabling HTTPS via Front Door managed document is not supported for noon/root domains (example: contoso.com). You lot can use your own certificate for this scenario. Delight continue with Option 2 for further details.
Option 2: Apply your own certificate
You can apply your own document to enable the HTTPS feature. This process is done through an integration with Azure Key Vault, which allows yous to shop your certificates securely. Azure Front end Door uses this secure mechanism to get your document and information technology requires a few extra steps. When you create your TLS/SSL certificate, you must create a complete certificate concatenation with an allowed document potency (CA) that is office of the Microsoft Trusted CA Listing. If y'all use a not-allowed CA, your request will be rejected. If a document without complete chain is presented, the requests which involve that certificate are not guaranteed to piece of work every bit expected.
Prepare your Azure Central vault account and certificate
- Azure Cardinal Vault: Yous must accept a running Azure Key Vault account under the same subscription as your Forepart Door that you want to enable custom HTTPS. Create an Azure Key Vault business relationship if you lot don't have one.
Alarm
Azure Forepart Door currently only supports Fundamental Vault accounts in the same subscription as the Front Door configuration. Choosing a Primal Vault nether a different subscription than your Front Door will effect in a failure.
- Azure Key Vault certificates: If you already accept a certificate, you can upload it directly to your Azure Cardinal Vault business relationship or you can create a new document straight through Azure Key Vault from one of the partner CAs that Azure Fundamental Vault integrates with. Upload your certificate as a certificate object, rather than a secret.
Note
For your ain TLS/SSL document, Forepart Door doesn't support certificates with EC cryptography algorithms. The certificate must have a complete certificate concatenation with leafage and intermediate certificates, and root CA must be part of the Microsoft Trusted CA listing.
Annals Azure Front end Door
Register the service principal for Azure Forepart Door as an app in your Azure Agile Directory using Azure PowerShell or Azure CLI.
Annotation
This action requires Global Administrator permissions, and needs to be performed merely once per tenant.
Azure PowerShell
-
If needed, install Azure PowerShell in PowerShell on your local machine.
-
In PowerShell, run the following command:
New-AzADServicePrincipal -ApplicationId "ad0e1c7e-6d38-4ba4-9efd-0bc77ba9f037" -Function Correspondent
Azure CLI
-
If need, install Azure CLI on your local car.
-
In CLI, run the following control:
SP_ID=$(az ad sp create --id 205478c0-bd83-4e1b-a9d6-db63a3e1e1c8 --query objectId -o tsv) az role consignment create --assignee $SP_ID --role Correspondent
Grant Azure Front Door access to your key vault
Grant Azure Front Door permission to access the certificates in your Azure Primal Vault account.
-
In your key vault account, under SETTINGS, select Access policies, then select Add together new to create a new policy.
-
In Select principal, search for ad0e1c7e-6d38-4ba4-9efd-0bc77ba9f037, and choose Microsoft.Azure.Frontdoor. Click Select.
-
In Secret permissions, select Become to allow Front Door to retrieve the certificate.
-
In Certificate permissions, select Get to allow Front Door to retrieve the certificate.
-
Select Add.
-
On the Admission policies folio, select Save.
Azure Front end Door can now admission this Key Vault and the certificates that are stored in this Key Vault.
Select the certificate for Azure Front end Door to deploy
-
Return to your Front Door in the portal.
-
In the list of custom domains, select the custom domain for which you desire to enable HTTPS.
The Custom domain folio appears.
-
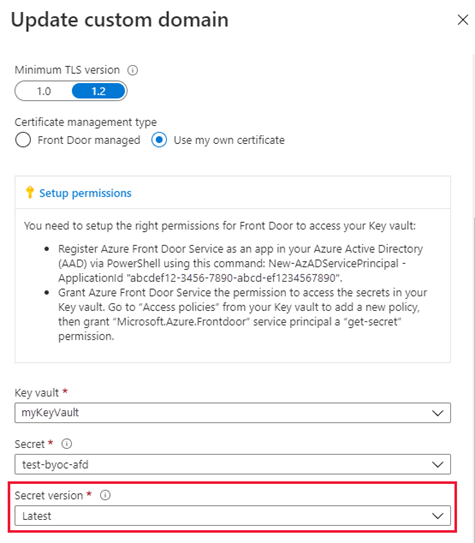
Under Document management type, select Utilize my own certificate.
-
Azure Front Door requires that the subscription of the Key Vault business relationship is the aforementioned as for your Front Door. Select a key vault, Hugger-mugger, and Secret version.
Azure Forepart Door lists the following information:
- The key vault accounts for your subscription ID.
- The secrets under the selected key vault.
- The available secret versions.
Note
In society for the certificate to be automatically rotated to the latest version when a newer version of the document is available in your Key Vault, please set the surreptitious version to 'Latest'. If a specific version is selected, you have to re-select the new version manually for document rotation. It takes up to 24 hours for the new version of the certificate/secret to exist deployed.
-
When you use your ain certificate, domain validation isn't required. Go on to Wait for propagation.
Validate the domain
If y'all already have a custom domain in use that gets mapped to your custom endpoint with a CNAME record or y'all're using your own certificate, continue to Custom domain is mapped to your Front Door. Otherwise, if the CNAME record entry for your domain no longer exists or it contains the afdverify subdomain, proceed to Custom domain is non mapped to your Front end Door.
Custom domain is mapped to your Front Door by a CNAME record
When you lot added a custom domain to your Front Door's frontend hosts, y'all created a CNAME tape in the DNS table of your domain registrar to map it to your Front Door's default .azurefd.net hostname. If that CNAME tape still exists and doesn't contain the afdverify subdomain, the DigiCert Certificate Say-so uses information technology to automatically validate ownership of your custom domain.
If you're using your own certificate, domain validation isn't required.
Your CNAME record should be in the following format, where Name is your custom domain name and Value is your Front end Door's default .azurefd.net hostname:
| Proper noun | Type | Value |
|---|---|---|
| <www.contoso.com> | CNAME | contoso.azurefd.net |
For more information about CNAME records, run across Create the CNAME DNS record.
If your CNAME tape is in the correct format, DigiCert automatically verifies your custom domain name and creates a defended document for your domain name. DigitCert won't transport you lot a verification email and you won't need to approve your request. The certificate is valid for 1 year and volition exist autorenewed before it expires. Continue to Wait for propagation.
Automated validation typically takes a few mins. If you lot don't run into your domain validated within an hour, open a support ticket.
Notation
If you have a Certificate Authority Authorization (CAA) record with your DNS provider, it must include DigiCert as a valid CA. A CAA record allows domain owners to specify with their DNS providers which CAs are authorized to upshot certificates for their domain. If a CA receives an club for a certificate for a domain that has a CAA record and that CA is not listed as an authorized issuer, it is prohibited from issuing the document to that domain or subdomain. For information nigh managing CAA records, see Manage CAA records. For a CAA record tool, see CAA Record Helper.
Custom domain is non mapped to your Forepart Door
If the CNAME record entry for your endpoint no longer exists or it contains the afdverify subdomain, follow the residuum of the instructions in this step.
Subsequently y'all enable HTTPS on your custom domain, the DigiCert CA validates ownership of your domain by contacting its registrant, according to the domain's WHOIS registrant data. Contact is made via the email address (by default) or the telephone number listed in the WHOIS registration. Y'all must complete domain validation before HTTPS will be active on your custom domain. Yous take 6 business days to approve the domain. Requests that aren't canonical within six business days are automatically canceled. DigiCert domain validation works at the subdomain level. You'll need to testify ownership of each subdomain separately.
DigiCert besides sends a verification email to other email addresses. If the WHOIS registrant data is private, verify that you can approve straight from one of the following addresses:
admin@<your-domain-name.com> ambassador@<your-domain-name.com> webmaster@<your-domain-name.com> hostmaster@<your-domain-proper noun.com> postmaster@<your-domain-name.com>
You lot should receive an email in a few minutes, similar to the following example, asking you to approve the asking. If you are using a spam filter, add together no-reply@digitalcertvalidation.com to its allowlist. Under certain scenarios, DigiCert may be unable to fetch the domain contacts from the WHOIS registrant information to send you an electronic mail. If yous don't receive an email inside 24 hours, contact Microsoft support.
When you select the approval link, y'all're directed to an online approval form. Follow the instructions on the form; you have two verification options:
-
Yous can approve all future orders placed through the same account for the same root domain; for instance, contoso.com. This approach is recommended if you lot programme to add more custom domains for the aforementioned root domain.
-
You can corroborate simply the specific host proper name used in this request. Extra approval is required for subsequent requests.
Afterwards approval, DigiCert completes the certificate cosmos for your custom domain name. The document is valid for one year and will be autorenewed before it's expired.
Wait for propagation
After the domain name is validated, it can take up to six-8 hours for the custom domain HTTPS feature to be activated. When the process is consummate, the custom HTTPS condition in the Azure portal is set up to Enabled and the four performance steps in the custom domain dialog are marked as complete. Your custom domain is now ready to use HTTPS.
Operation progress
The following table shows the operation progress that occurs when y'all enable HTTPS. Subsequently you enable HTTPS, four functioning steps announced in the custom domain dialog. As each stride becomes active, more than substep details appear under the step as information technology progresses. Not all of these substeps will occur. After a footstep successfully completes, a dark-green check marking appears adjacent to it.
| Operation step | Performance substep details |
|---|---|
| one Submitting request | Submitting request |
| Your HTTPS asking is being submitted. | |
| Your HTTPS request has been submitted successfully. | |
| ii Domain validation | Domain is automatically validated if information technology's CNAME mapped to the default .azurefd.internet frontend host of your Forepart Door. Otherwise, a verification asking will be sent to the email listed in your domain'due south registration record (WHOIS registrant). Verify the domain as presently every bit possible. |
| Your domain ownership has been successfully validated. | |
| Domain ownership validation asking expired (customer likely didn't answer within half dozen days). HTTPS won't be enabled on your domain. * | |
| Domain ownership validation asking was rejected by the client. HTTPS won't exist enabled on your domain. * | |
| 3 Certificate provisioning | The document say-so is currently issuing the document needed to enable HTTPS on your domain. |
| The document has been issued and is currently existence deployed for your Front Door. This process could accept from several minutes to an hour to consummate. | |
| The document has been successfully deployed for your Front end Door. | |
| 4 Complete | HTTPS has been successfully enabled on your domain. |
* This message doesn't appear unless an fault has occurred.
If an fault occurs before the request is submitted, the following error message is displayed:
We encountered an unexpected error while processing your HTTPS request. Delight try once again and contact support if the issue persists. Frequently asked questions
-
Who is the certificate provider and what type of certificate is used?
A dedicated/single document, provided by Digicert, is used for your custom domain.
-
Practice you apply IP-based or SNI TLS/SSL?
Azure Front Door uses SNI TLS/SSL.
-
What if I don't receive the domain verification email from DigiCert?
If you have a CNAME entry for your custom domain that points directly to your endpoint hostname (and you aren't using the afdverify subdomain name), you won't receive a domain verification email. Validation occurs automatically. Otherwise, if you don't have a CNAME entry and you haven't received an email within 24 hours, contact Microsoft back up.
-
Is using a SAN certificate less secure than a dedicated certificate?
A SAN certificate follows the aforementioned encryption and security standards as a dedicated certificate. All issued TLS/SSL certificates use SHA-256 for enhanced server security.
-
Exercise I need a Certificate Authority Authorization tape with my DNS provider?
No, a Certificate Authority Authorization record isn't currently required. However, if you do accept i, it must include DigiCert as a valid CA.
Clean up resources
In the preceding steps, you enabled the HTTPS protocol on your custom domain. If you no longer desire to employ your custom domain with HTTPS, you lot tin can disable HTTPS by doing theses steps:
Disable the HTTPS feature
-
In the Azure portal, scan to your Azure Front Door configuration.
-
In the listing of frontend hosts, select the custom domain for which yous want to disable HTTPS.
-
Click Disabled to disable HTTPS, then click Relieve.
Wait for propagation
After the custom domain HTTPS characteristic is disabled, it tin can accept upwards to half-dozen-8 hours for it to take effect. When the process is complete, the custom HTTPS status in the Azure portal gets set to Disabled and the 3 operation steps in the custom domain dialog are marked every bit consummate. Your custom domain can no longer utilise HTTPS.
Operation progress
The following table shows the operation progress that occurs when you disable HTTPS. Afterward you disable HTTPS, three performance steps appear in the Custom domain dialog. As each stride becomes active, more details appear under the stride. Afterwards a step successfully completes, a light-green bank check mark appears next to information technology.
| Operation progress | Operation details |
|---|---|
| ane Submitting request | Submitting your request |
| ii Certificate deprovisioning | Deleting certificate |
| 3 Complete | Certificate deleted |
Next steps
In this tutorial, you learned how to:
- Upload a certificate to Key Vault.
- Validate a domain.
- Enable HTTPS for your custom domain.
To learn how to set up a geo-filtering policy for your Front end Door, keep to the next tutorial.
Feedback
Submit and view feedback for
How To Return Account And Its Associated Contacts In Apex Rest Services,
Source: https://docs.microsoft.com/en-us/azure/frontdoor/front-door-custom-domain-https
Posted by: dickersonloste1954.blogspot.com


0 Response to "How To Return Account And Its Associated Contacts In Apex Rest Services"
Post a Comment